Flareon10 X
Flareon 10 - X
As I can’t physically dedicate myself to only one project at a time, I decided to check out the latest version of the long running Flare-On CTF.
Opening up the folder provided, we are met with a lot of files. As I wouldn’t call myself an expert, or even moderately experienced in Reverse Engineering, this is enough to start psyching me out 😅.
But onwards I went and opened up X.exe and found this pretty cute interface.

So intuitively I assume that we’ll have to find a two digit code to crack this challenge open.
While the final solution was pretty simple, it taught me an important lesson in tool choice. While dnSpy should have been able to handle this, it makes the important part of this binary (for us) mangled, and can not process it correctly (it’s more likely that I don’t know how to use it correctly but at the same time, I just loaded X.dll and did nothing fancy)
After despairing for a bit and thinking that this is the first challenge, it can not be that hard, I checked the official solutions and saw that they were using dotPeek for their decompiling purposes. So, after loading it up in it, a much friendlier function appeared 😅
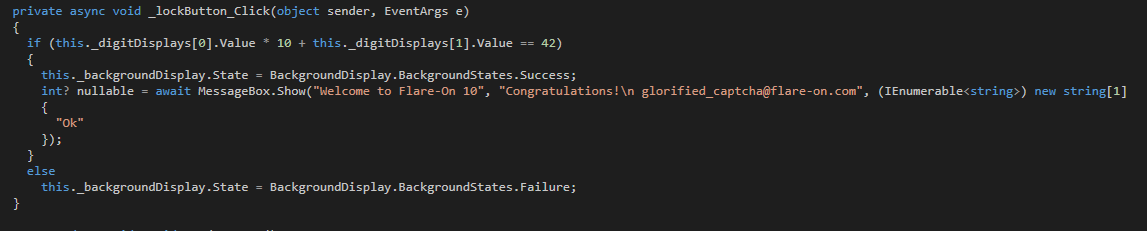
As we can see from the code, all we need to solve this challenge is to input the number 42 and we should be golden.

Soooo, Mandiant (the creators of the Flareon project) have said that they intended to make this year the hardest they’ve ever done, so let’s see how long I can make it before I can’t do them by myself and need to greatly refer to their write-ups.
Happy hacking,
0x42ernardo